Attack Tree
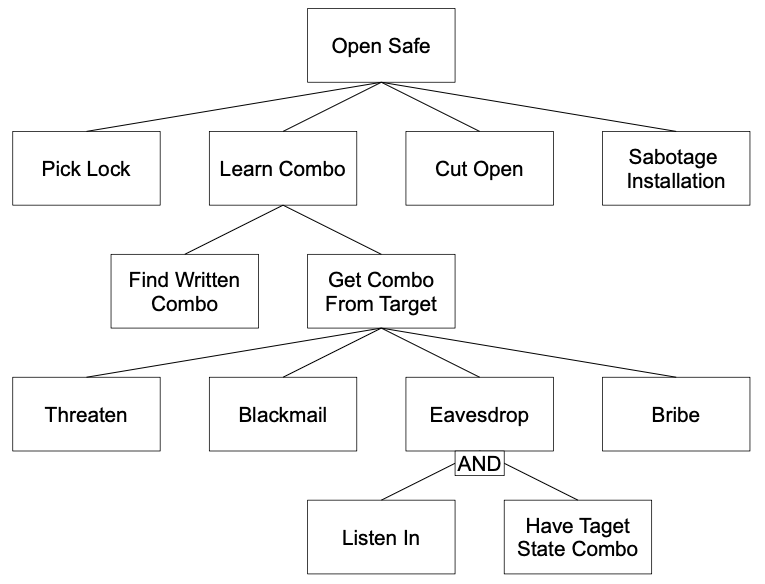
Attack trees provide a formal, methodical way of describing the security of systems, based on varying attacks. Basically, you represent attacks against a system in a tree structure, with the goal as the root node and different ways of achieving that goal as leaf nodes.
Before we can construct an attack tree we first need to identify the possible attack goals. Please note that each goal forms a separate tree, although they might share subtrees and nodes.
- Think of all attacks against each goal and add them to a tree. Repeat this process down the tree until you are done:
TIP
Give the tree to someone else, have them think about the process and add any nodes they think of.
- Determine which elementary attacks are Possible and Impossible:
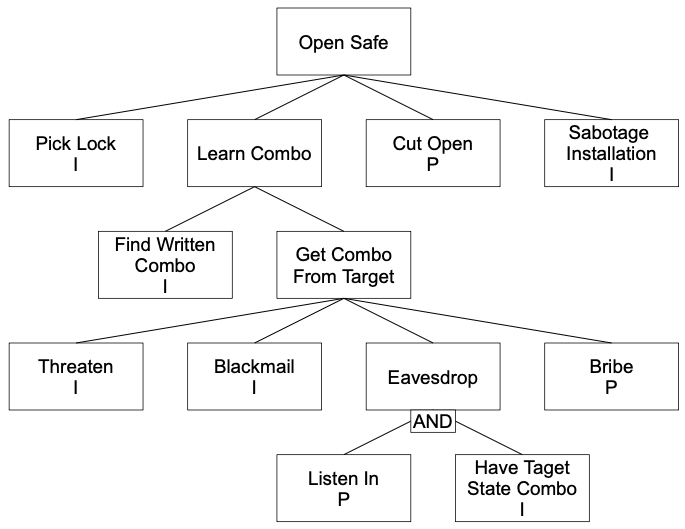
- Determine which attack paths can realize the goal:
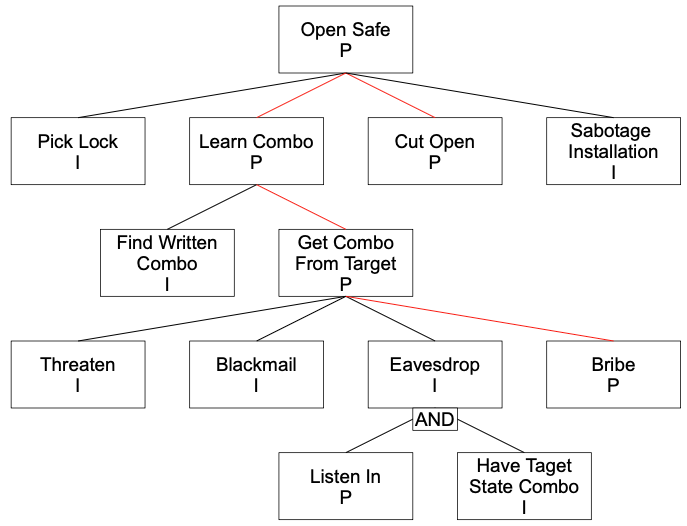
The same approach can also be used to analyste other properties such as the cost of a attack: 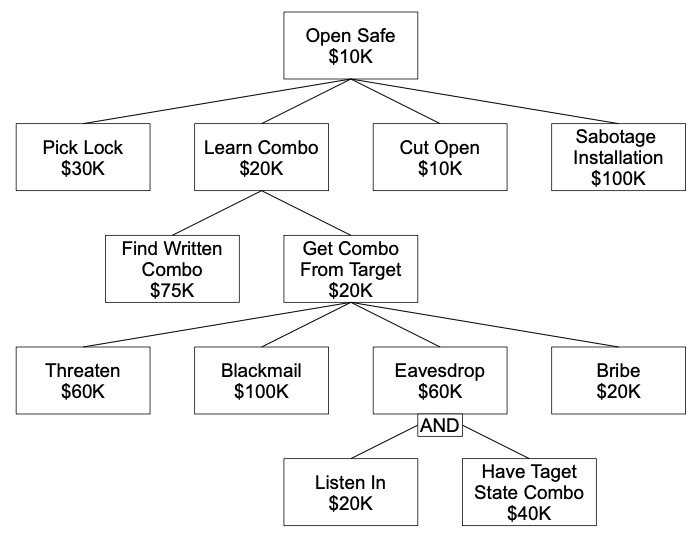
Relevant Note(s): Fault Tree Analysis