Unified Kill Chain
The Unified Kill Chain unites the Cyber Kill Chain with MITRE ATT&CK and extends on them by addressing their critiques:
- Cyber Kill Chain
- is perimeter- and malware-focused. As such attack vectors and attacks that occur behind the organizational perimeter are out of scope
- attack phases may be bypassed
- MITRE ATT&CK's tactics are time-agnostic
- explicating the role of users by modelling Social Engineering
- recognizing the crucial role of choke points in attacks by modelling Pivoting
- covering the compromise of the CIA Triad
- clarifying the overarching objectives of threat actors
Instead of focusing on thwarting attacks at the earliest point in time, Defense in Depth strategies that focus on attack phases that occur with a higher frequency or that are vital for the formation of an attack path are thus expected to be more successful.
These insights support the development (or realignment) of Defense in Depth strategies that adopt the Assumed Breach principles and to optimize the return on investment (ROI) of their security measures.
Phases of the Unified Kill Chain

Multiple tactical phases of an attack can be combined to achieve intermediate goals. The next sections will describe how the individual phases of the Unified Kill Chain are typically combined by attackers to achieve intermediate goals in the phased progression towards achieving their final objectives.
If one of the tactics of a phase fail, the attempt to complete the phase may also fail. However, an attacker may change tactics, or adjust the specific techniques used within a tactic, in follow-up attacks until the strategic goal is achieved.
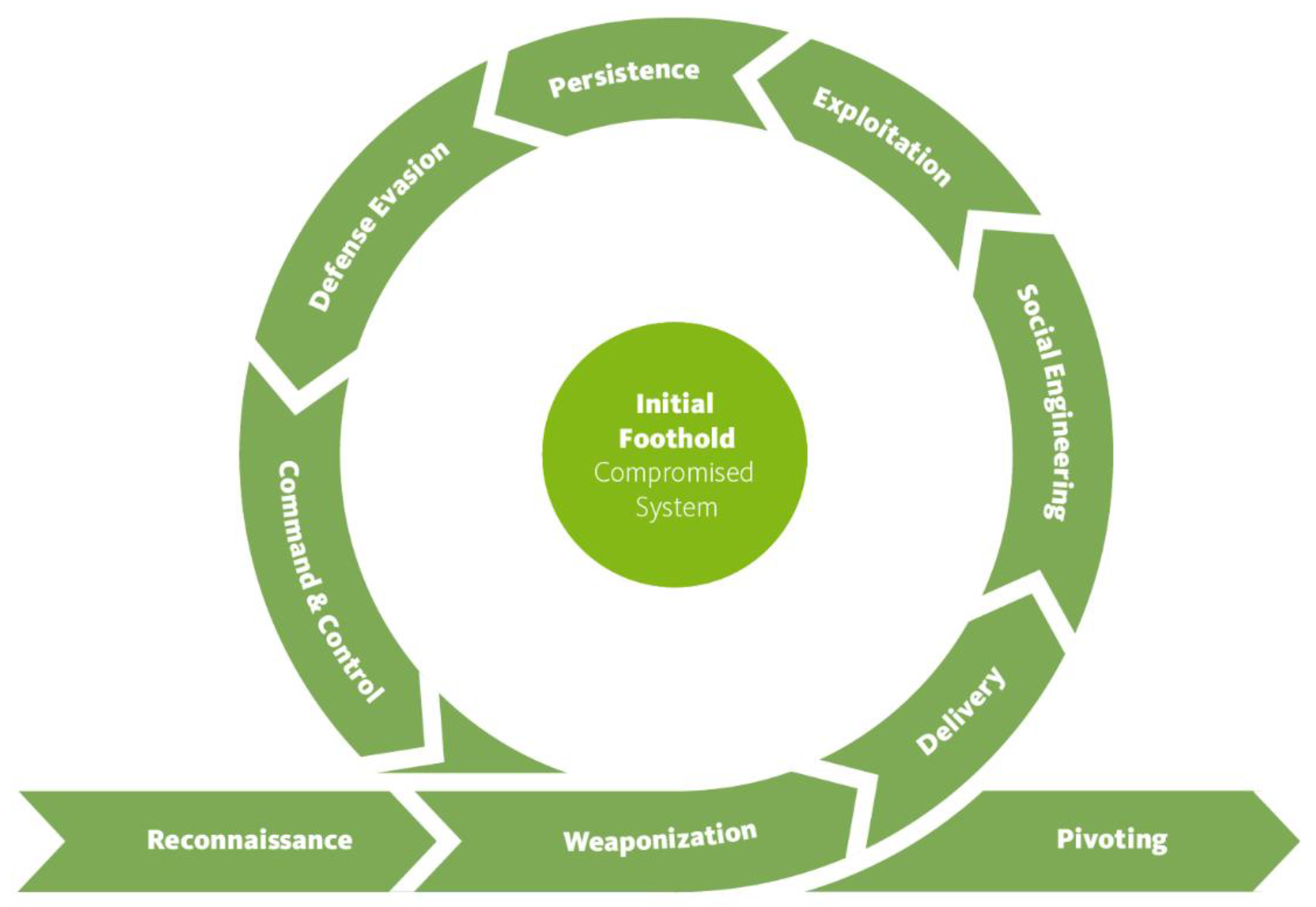
Initial foothold
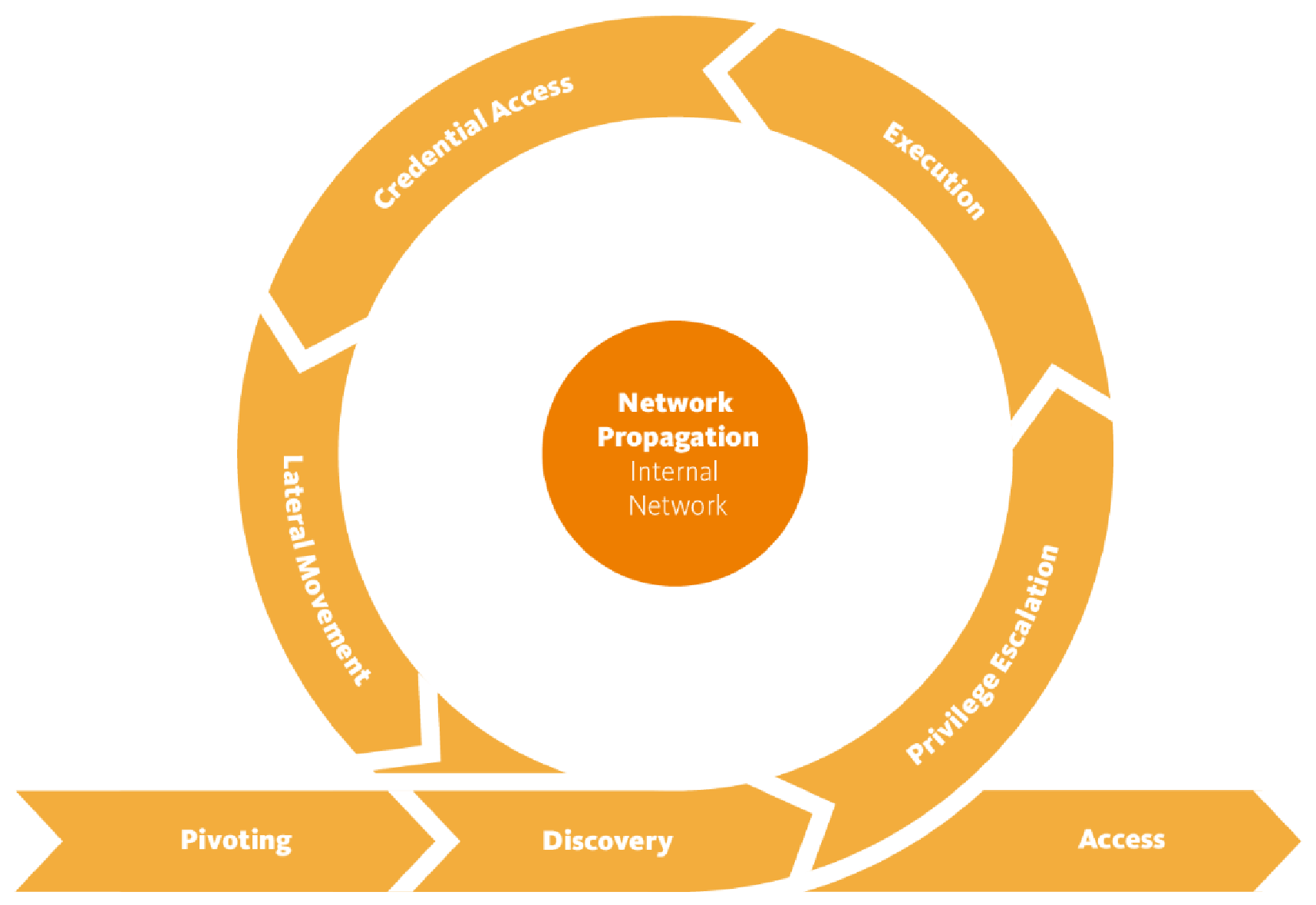
Network propagation
If access to the compromised system directly allows an attacker to take action on the final objectives of the attack, then an attacker can move straight to Action on Objectives. If the objectives require further access to systems and data, an attacker will be forced to propagate through the internal network first.
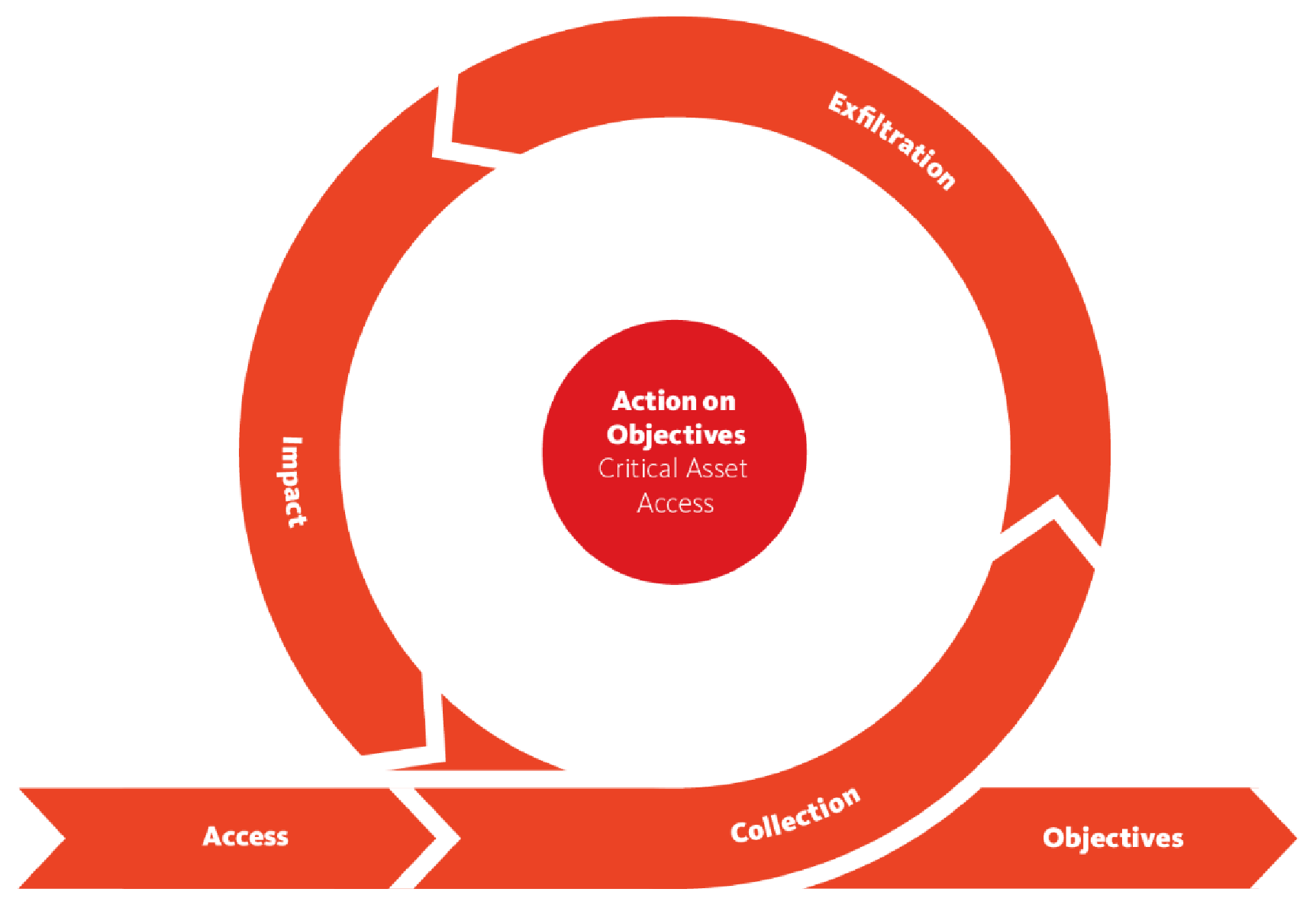
Action on Objectives
Collectively the phases Collection, Exfiltration and Impact can be used to describe all compromises of the CIA Triad. These activities can be performed continuously or periodically and can thus also be regarded as a loop.
Relevant Notes(s): Incident Response Detection Engineering Threat Modeling