Threat Hunting Maturity Model
With that definition of hunting in mind, let's consider what makes a good hunting program. There are three factors to consider when judging an organization's hunting ability:
- the quality of the data they collect for hunting
- the tools they provide to access and analyse the data
- the skills of the analysts who actually use the data and the tools to find security incidents
Of these factors, the analysts' skills are probably the most important, since they are what allows them to turn data into detections. That's why each level of the Hunting Maturity Model (HMM) starts with a statement of the level of analytic capability that is typically found at that level.
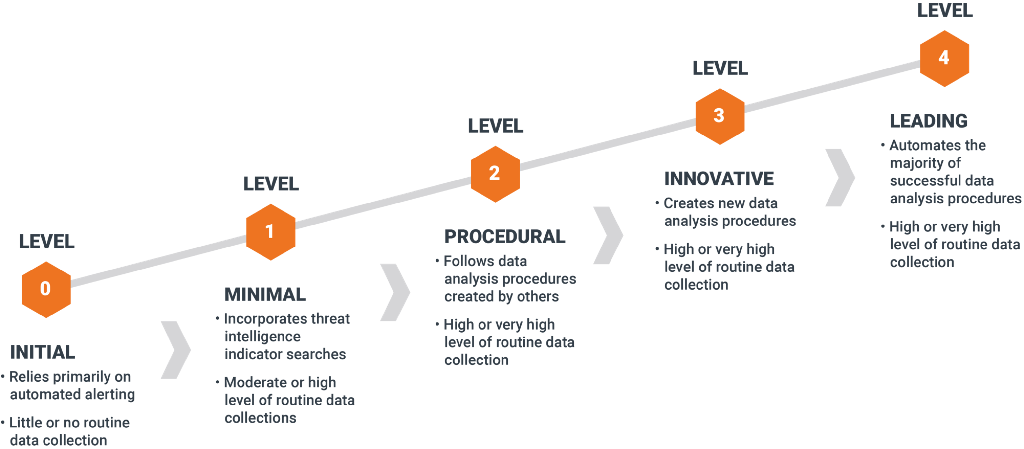
HMM0 "Initial"
At HMM0, an organization relies primarily on automated alerting tools such as IDS, SIEM or antivirus to detect malicious activity across the enterprise. They may incorporate feeds of signature updates or threat intelligence indicators, and they may even create their own signatures or indicators, but these are fed directly into the monitoring systems. The human effort at HMM0 is directed primarily toward alert resolution.
HMM0 organizations also do not collect much information from their IT systems beyond the bare minimum needed to drive their automated alerting. Thus, even if they were to somehow acquire hunting expertise (perhaps by hiring a consultant or by making a strategic hire), their ability to actually hunt would be severely limited.
Organizations at HMM0 are not considered to be capable of hunting.
HMM1 "Minimal"
An organization at HMM1 still relies primarily on automated alerting to drive their incident response process, but they are actually doing at least some routine collection of IT data. These organizations often aspire to intel-driven detection (that is, they base their detection decisions in large part upon their available threat intelligence). They often track the latest threat reports from a combination of open and closed sources.
HMM1 organizations routinely collect at least a few types of data from around their enterprise, and some may actually collect a lot. Thus, when new threats come to their attention, analysts are able to extract the key indicators from these reports and search historical data to find out if they have been seen in at least the recent past.
Because of this search capability, HMM1 is the first level in which any type of hunting occurs, even though it is minimal.
HMM2 "Procedural"
Organizations at HMM2 are able to learn and apply procedures developed by others, and may make minor changes, but are not yet capable of creating wholly new procedures themselves. Procedures meaning the combination of an expected type of input data with a specific analysis technique to discover a single type of malicious activity (e.g. detecting malware by gathering data about which programs are set to automatically start on hosts across the enterprise and using least-frequency analysis to find suspicious binaries).
HMM2 organizations routinely apply these procedures, if not on a strict schedule, then at least on a somewhat regular basis.
Most of the commonly available procedures rely in some way on Least-Frequency Analysis (as of October 2015, anyway). This technique is only effective if there is data from many different hosts. Therefore, HMM2 organizations usually collect a large (sometimes very large) amount of data from across the enterprise.
HMM2 is the most common level of capability among organizations that have active hunting programs.
HMM3 "Innovative"
HMM3 organizations have at least a few hunters who understand a variety of different types of data analysis techniques and are able to apply them to identify malicious activity. Instead of relying on procedures developed by others, these organizations are usually the ones who are creating and publishing the procedures. Analytic skills may be as simple as basic statistics or involve more advanced topics such as Linked Data Analysis, Data Visualization or Machine Learning. The important point is that the analysts are able to apply the techniques to create repeatable procedures, which are documented and performed on a frequent basis.
Data collection at HMM3 tends to be similar to that at HMM2, though perhaps more advanced, since the continual focus on developing new techniques tends to drive the analysts into new data sources over time.
HMM3 organizations can be quite effective at finding and combating threat actor activity. However, as the number of hunting processes they develop increases over time, they may face scalability problems trying to perform them all on a reasonable schedule unless they increase the number of available analysts to match.
HMM4 "Leading"
An HMM4 organization is essentially the same as one at HMM3, with one important difference: automation. At HMM4, any successful hunting process will be operationalized and turned into automated detection. This frees the analysts from the burden of running the same processes over and over, and allows them instead to concentrate on improving existing processes or creating new ones.
HMM4 organizations are extremely effective at resisting adversary actions. The high level of automation allows them to focus their efforts on creating a stream of new hunting processes, which results in constant improvement to the detection program as a whole. They try new ideas all the time, knowing that some won’t pan out but others will. They are inventive, curious and agile, qualities you can’t get from a purely automated detection product. Although a good hunting platform can certainly give your team a boost, you can’t buy your way to HMM4.
[1] [2]
Relevant Note(s): Threat Hunting