Threat Hunting Loop
The hunting loop is a simple but effective step-by-step process that can enhance an organization’s control over its own defence.
Hunting is most effective when it is used together with other more traditional security systems, complementing the detection efforts and Perimeter Security that most organizations already have in place.
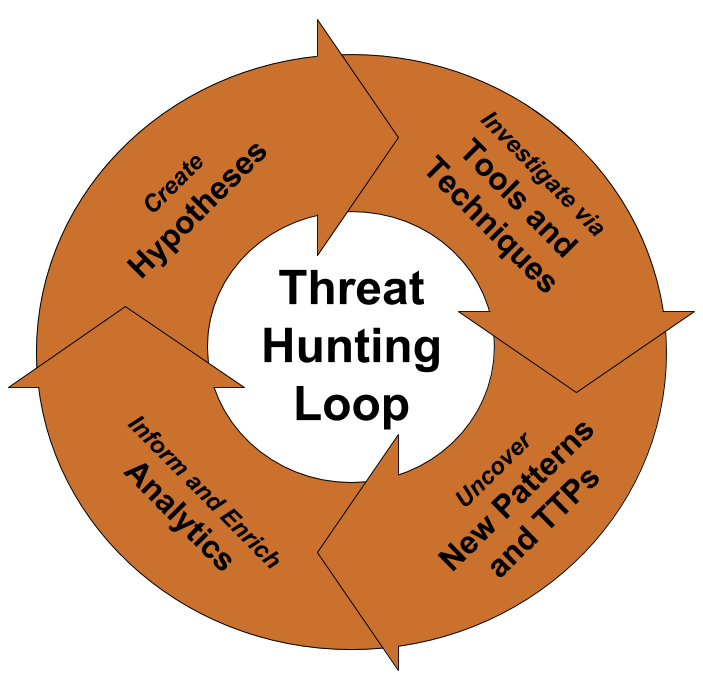
A hunt starts with creating a hypothesis, or an educated guess, about some type of activity that might be going on in your IT environment. An example of a hypothesis could be that users who have recently travelled abroad are at elevated risk of being targeted by state-sponsored threat actors, so you might begin your hunt by planning to look for signs of new malware on their laptops or assuming that their accounts are being misused around your network. Hypotheses are typically formulated by analysts based on any number of factors, including friendly and threat intelligence. There are various ways that a hunter might form a hypothesis. Often this involves laying out attack models and the possible tactics a threat might use, determining what would already be covered by automated alerting systems, and then formulating a hunting investigation of what else might be happening.
Hypotheses are investigated via various tools and techniques, including Linked Data Search and visualization. Effective tools will leverage both raw and linked data analysis techniques such as visualization, Statistical Analysis or Machine Learning to fuse disparate cybersecurity datasets. Linked Data Analysis is particularly effective at laying out the data necessary to address the hypotheses in an understandable way, and so is a critical component for a hunting platform. Linked data can even add weights and directionality to visualizations, making it easier to search large data sets and use more powerful analytics. Many other complementary techniques exist, including row-oriented techniques such as Stack Counting and Data Point Clustering. Analysts can use these techniques to easily discover new malicious patterns in their data and reconstruct complex attack paths to reveal an attacker’s Tactics, Techniques & Procedures.
Tools and techniques uncover new malicious patterns of behaviour and adversary TTPs. This is a critical part of the hunting cycle. An example of this process could be that a previous investigation revealed that a user account has been behaving anomalously, with the account sending an unusually high amount of outbound traffic. After conducting a Linked Data investigation, it is discovered that the user’s account was initially compromised via an exploit targeting a third party service provider of the organization. New hypotheses and analytics are developed to specifically discover other user accounts affiliated with similar third party service providers.
Finally, successful hunts form the basis for informing and enriching automated analytics. Don’t waste your team’s time doing the same hunts over and over. Once you find a technique that works to bring threats to light, automate it so that your team can continue to focus on the next new hunt. Information from these hunts can also be used to improve existing detection mechanisms. For example, you may uncover information that leads to new Threat Intelligence or Indicators of Compromise. You might even create some Friendly Intelligence. The more you know about your own network, the better you can defend it, so it makes sense to try to record and leverage new findings as you encounter them on your hunts.
[1]
Relevant Note(s): Threat Hunting