Tactics, Techniques & Procedures
The term "TTP" was born out of the military (exact date & original source unknown), and is an acronym for "Tactics, Techniques, and Procedures", of which each have their own individual definitions we'll cover here in a bit. TTP's are formally defined for us by The United States Department of Defense Joint Chiefs of Staff, Joint Publication 1-02 (JP 1-02) entitled "Department of Defense Dictionary of Military and Associated Terms", in which it states:
- Tactics: The employment and ordered arrangement of forces in relation to each other.
- Techniques: Non-prescriptive ways or methods used to perform missions, functions, or tasks.
- Procedures: Standard, detailed steps that prescribe how to perform specific tasks.
I like to think of these as a hierarchy of specificity, going from the most broad (Tactics) to the most specific (Procedures).
How to apply this to Information/Cyber Security with context
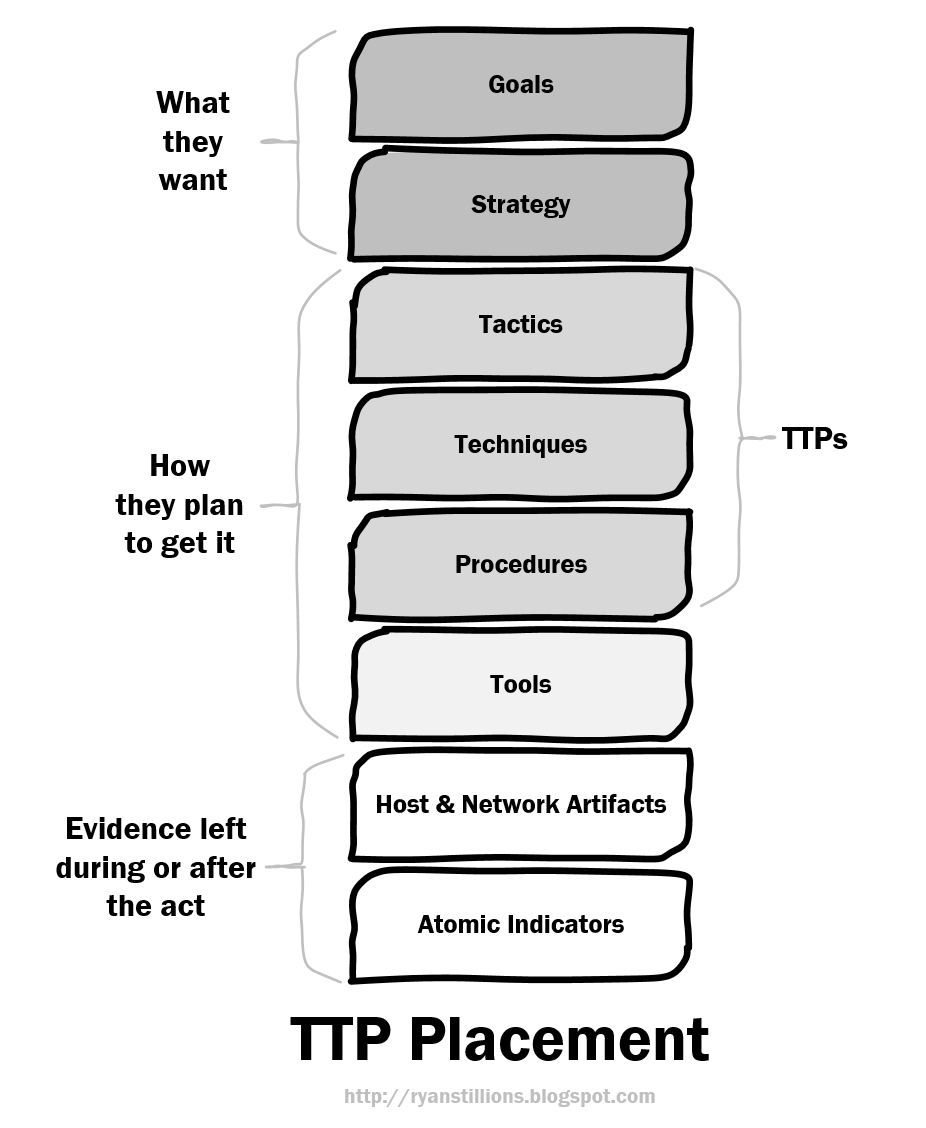
Goals are the true intentions behind the adversary's acts. They are nearly impossible to detect (directly) in an environment, but most certainly can be collected via an intelligence operation.
Strategy is where the adversary actually begins to establish one or more viable means of obtaining those goals.
Sometimes Goals & Strategy are collectively called campaigns.
Or, in layman terms, "What the adversary actually wants".
Tactics refer to the art or skill of employing available means to accomplish an end. Tactics are most often observed in high level narratives like "we see the adversary compromise the victim by performing SQL injection against their public facing web server". The tactic in that statement is "SQL injection against public facing web server". It is specific, yet does not prescribe the specific Technique, Procedure, or Tool used by the adversary, nor does it mention the resulting Artefacts or IOCs from employing the tactic. Tactics should be thought of as what the adversary is doing, typically at a specific stage of an attack, without getting into the how's, why's, and binary bits.
Techniques are the way that a person performs basic physical movements or skill, but most importantly they are non-prescriptive, meaning there is no procedural sequencing with techniques. They simply describe the unique ways or methods used to perform missions, functions, or tasks specific to the actual person performing the work. For example, a given actor may have a habit of repeating a specific typo, or use a specific keyboard pattern sequence when passing a password into a command line argument. This person may be performing the exact same procedure as the operator sitting next to them, yet their background, skills, habits, and personal tendencies will mould their unique techniques.
This may not seem immediately relevant to some, but it can mean everything to an Intelligence Analyst performing campaign analysis over a set of multiple incidents, attempting to draw out the most subtle of distinguishing factors.
Procedures are a series of actions that are done in a certain way or order, or put different as standard, detailed steps that prescribe how to perform specific tasks. Procedures are not observations of individual atomic indicators, but the sequential observation of two or more indicators that establish a trend indicative of a procedure being performed. An example would be an adversary running net time, followed by the AT.exe command to schedule a job to kick off just one minute after the current local time of the victim system. Individually, these are each indicators, but when chained together they become a procedure.
Tools are exactly what you would expect. Any tool, malicious or benign, that the adversary uses to complete his or her objective falls in this element.
What's left are the the Host & Network Artifacts and Atomic Indicators which constitute the evidence left during or after the act of attempting (successfully or not) to fulfill any part of their goals. The key distinguishing factor in these elements is that they are indicators that are left behind as a result of the higher level TTPs taking place. They're the breadcrumbs on which most all detection technology is based, so it's important to not underestimate the significant contribution of these next two levels. It's through the data collected at these next two levels that the above levels can be observed. Unfortunately, too much focus gets placed on these levels and we hyper-focus on just Artifacts and IOCs. We often fail to retain necessary relationships and surrounding context that facilitates our understanding of the higher elements.
Host & Network Artifacts are an extremely large element that encompasses any artifact left behind at the host, network, or event data level which are indicative of a tool being used or an identified TTP. Host & Network Artifacts also contain context such as where and how they were observed, and usually include one or more atomic indicators. Examples of these could be anything from registry entries, to prefetch entries, to mutexes found in memory, to a specially crafted HTTP POST transaction for an outbound stage-1 backdoor check-in seen in network traffic.
Atomic Indicators are the lowest possible denominator of information. They represent the lowest decomposable level of information and metadata related to tool usage or an identified TTP. These are often organized by indicator-type, tuck nicely into tables and rows, and get passed around the community as "threat intelligence" though in reality it's largely contextless strings of data. Examples of these include IPs, domains, email addresses, file hashes, or even regular expression patterns that match atomic indicators.
[1] [2] [3]
Relevant Note(s): Detection Maturity Level Model Pyramid of Pain, Tactical to Functional