Detection Spectrum
Instead of using loaded terms like brittle, simple, or bad to describe detection logic, detections fall on a “detection spectrum” where one end represents “precise” logic while the other represents “broad” logic.
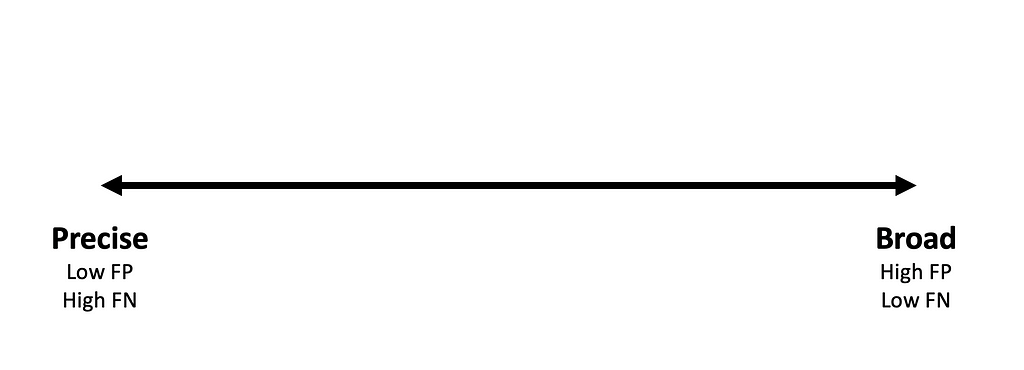
The precise end of the spectrum represents detection logic that values the reduction of potential false positives over the reduction of potential false negatives. E.g.: A detection looking for a malicious tool based on its hash. By definition, this approach is unlikely to produce false positives (a legitimate event that collides with the malicious binaries hash), but false negatives (a malicious event that does not share this hash value) are very likely.
Broad detections value the reduction of potential false negatives over the reduction of potential false positives. E.g.: A detection focusing on the Kerberos TGS-REQ network request to detect Kerberoasting.
Broad detections are not silver bullets. They typically create a more significant triage burden than precise detections. This is something that an organization must consider when they are weighing their desire for coverage against their resourcing.
In practise, given sufficient human and technical resources, it makes sense writing multiple detections per attack technique along the spectrum and then prioritizing the created alerts according to their precision. For more, see Comprehensive Detection.
Relevant Note(s): Capability Abstraction