Detection Backlog Prioritization
Please note that each organization is unique and will have to adapt the concepts in this note to their needs.
Inputs
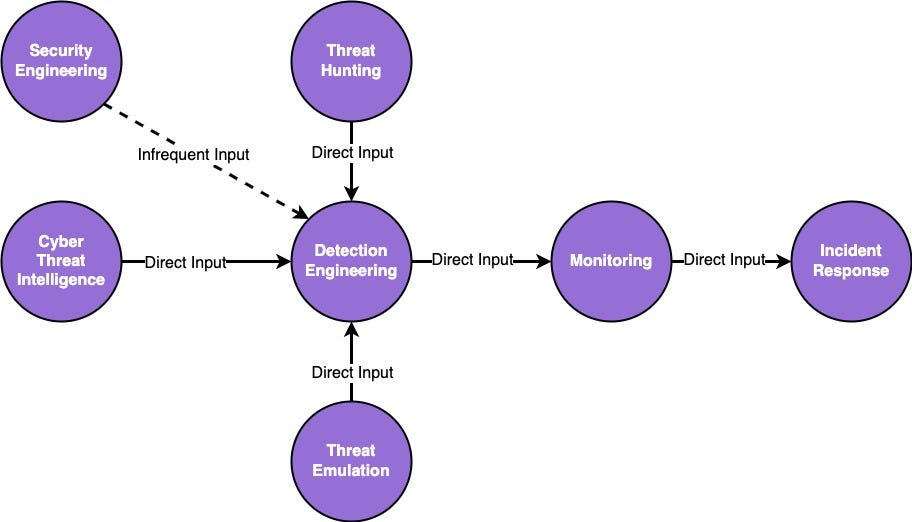
Each of the Backlog Items should at least contain:
- Title
- Date
- Description
- Technique ID
- Input Function
- Priority
- Status
And could look something like this:
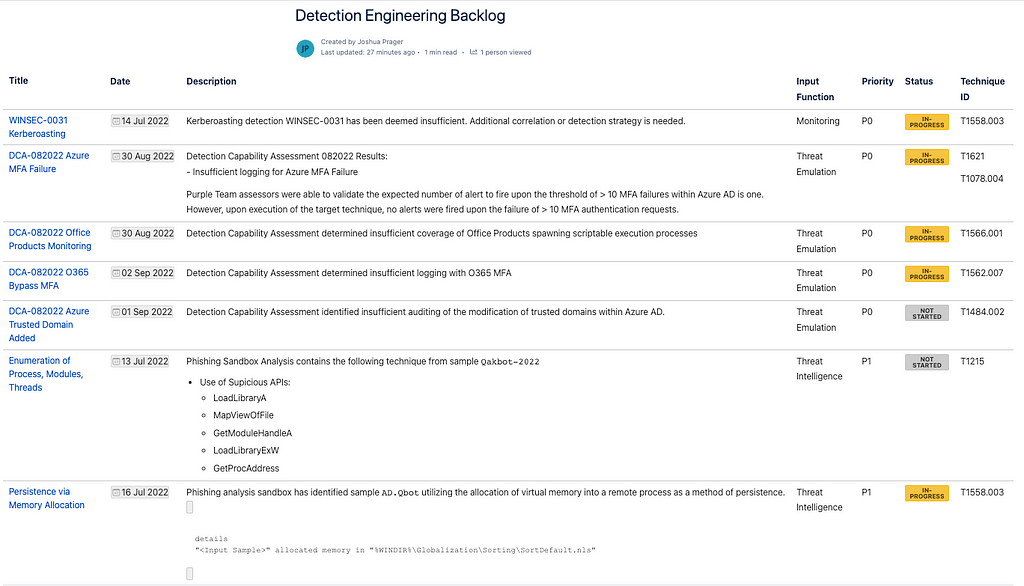
Prioritization
The process of determining the prioritization is subjective and may contain overlap. For example, detection engineering may receive an external intelligence report that identifies a critical TTP for which your organization is vulnerable. In this scenario, the original input (external intelligence) would indicate a level of priority 2, but the information contained in the report would be a level of priority 0. If this pertinent information is known upon prioritization; always default to the higher-priority level.
Detection prioritization requires industry and organizational context, which aids the prioritization lead in minimizing errors. These errors could lead to unidentified and un-remediated vulnerabilities sitting in the backlog. Especially, if the input is from a less mature function and does not contain needed operational information.
Priority 0
The highest priority are then known target techniques for which the organization has the least amount of coverage. They come out of gap analysis, purple team assessments, and defensive capability assessments and the like and are cause for immediate concern.
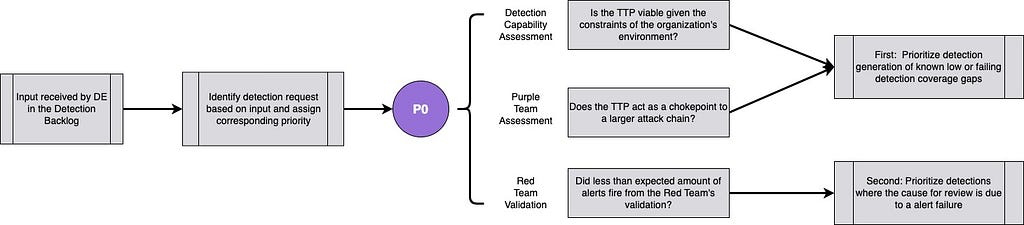
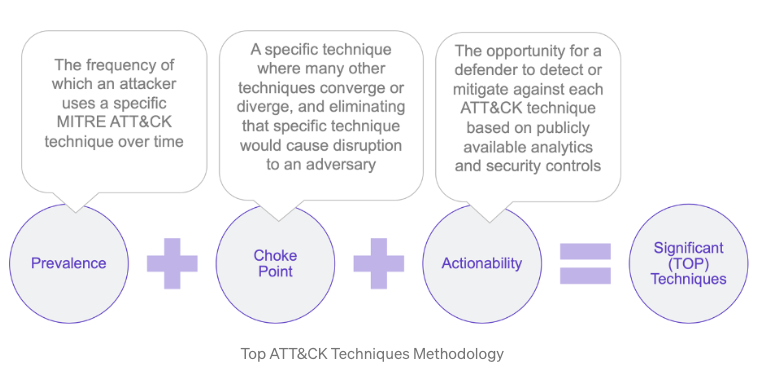
If this Priority needs to be ordered further, a look into the MITRE ATT&CK Top Techniques Calculator or the underlying Excel Sheet can be useful.
They've collected metrics on the prevalence of an attack technique as it relates to adversaries and its frequency of use over historical evidence.
Priority 1
Detections in this category come from Internal Intelligence and are techniques derived from identified phishing attempts, incidents, and honeynets.
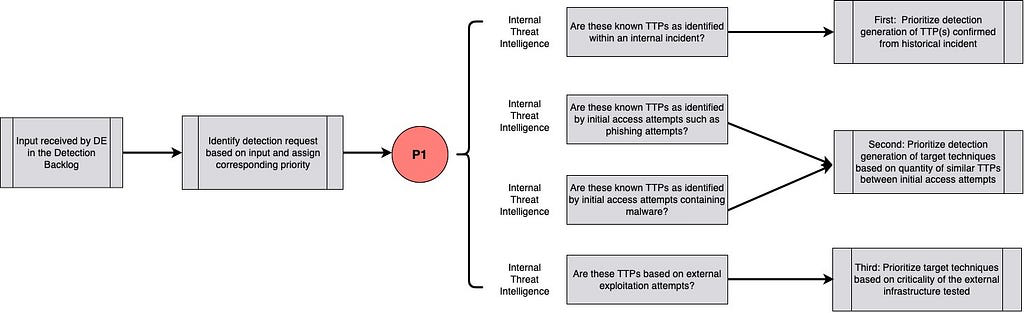
Priority 2
Here the input is External Intelligence relevant to the organization (e.g.: similar industry, business, suppliers/partners, software stack, etc.)
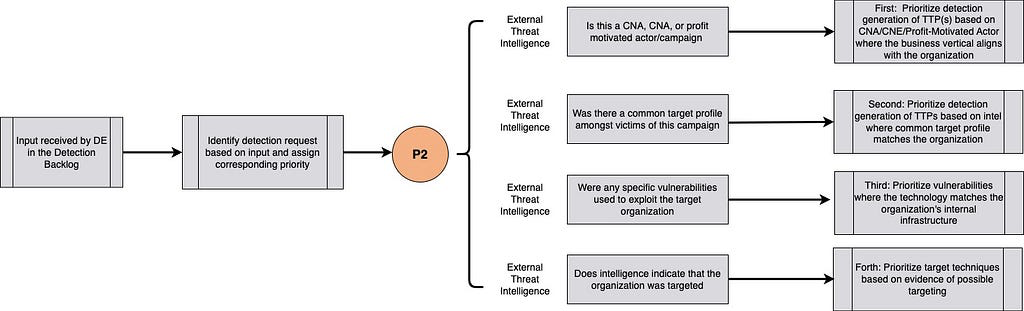
Priority 3
Sub-Technical Synonyms, gathered through Capability Abstraction, of identified in Internal and External Intelligence.
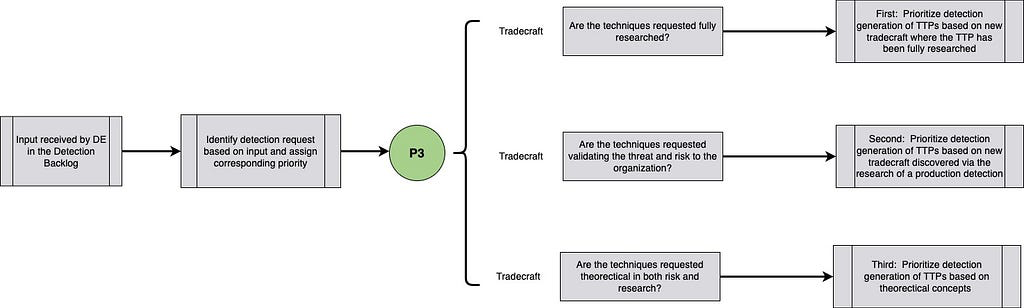
Priority 4
Writing of queries for non-threat detection-based concerns like operational metrics and key performance indicators. The requests for this type of alert often make their way to the detection backlog due to the expertise in query development and data aggregation that most detection engineers have.
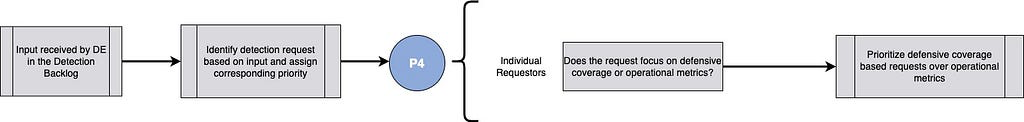
Relevant Note(s):