Cyber Kill Chain
A kill chain is a systematic process to target and engage an adversary to create desired effects. U.S. military targeting doctrine defines the steps of this process as F2T2EA:
- find adversary targets suitable for engagement
- fix their location;
- track and observe
- target with suitable weapon or asset to create desired effects
- engage adversary
- assess effects
This is an integrated, end-to-end process described as a “chain” because any one deficiency will interrupt the entire process.
Expanding on this concept, this paper presents a new kill chain model, one specifically for intrusions. The essence of an intrusion is that the aggressor must:
- develop a payload to breach a trusted boundary
- establish a presence inside a trusted environment
- and from that presence, take actions towards their objectives, be they moving laterally inside the environment or violating the CIA Triad of a system in the environment.
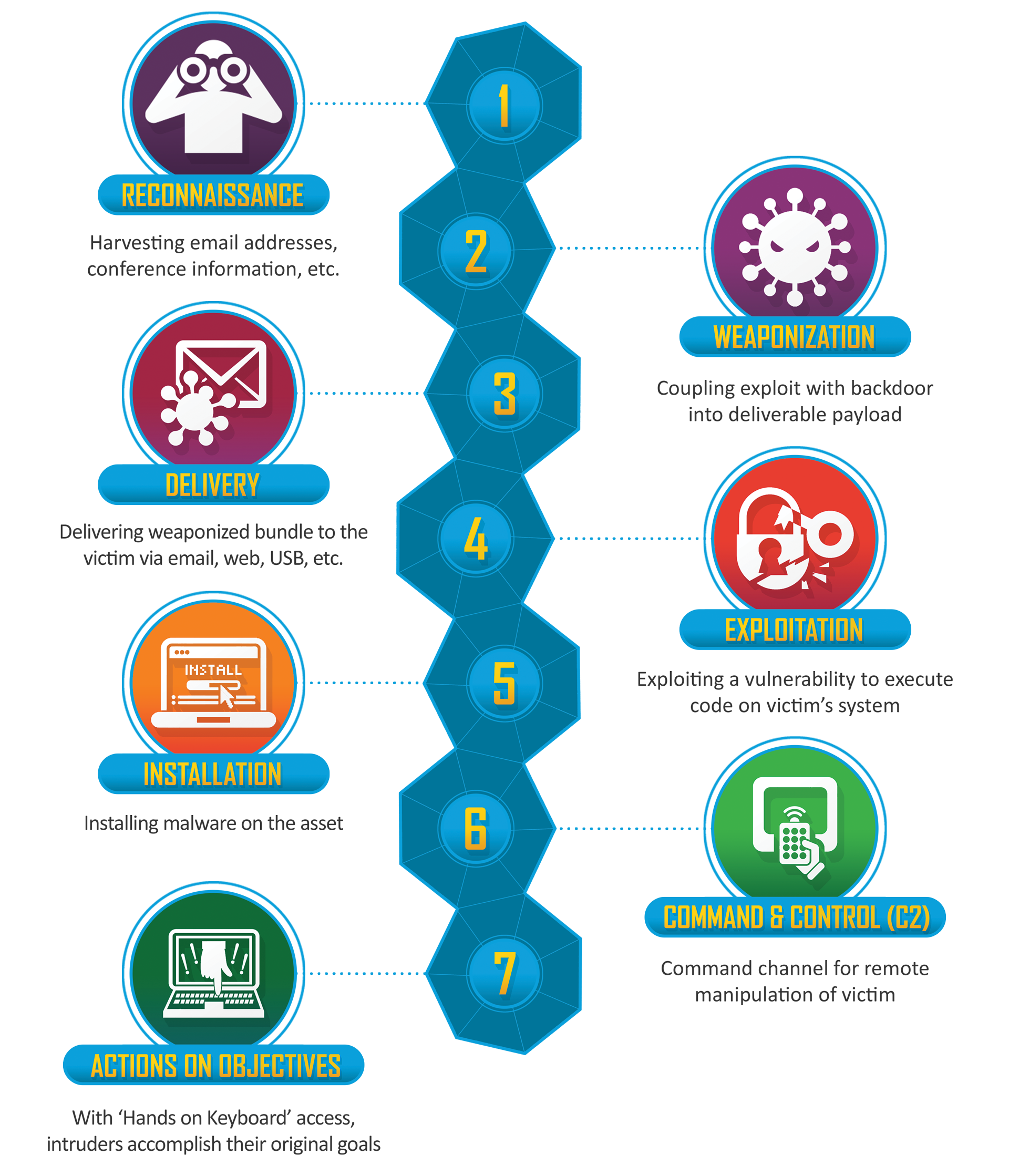
The intrusion kill chain is defined as reconnaissance, weaponization, delivery, exploitation, installation, command and control (C2), and actions on objectives.
- Reconnaissance - Research, identification and selection of targets, often represented as crawling Internet websites such as conference proceedings and mailing lists for email addresses, social relationships, or information on specific technologies.
- Weaponization - Coupling a remote access trojan with an exploit into a deliverable payload, typically by means of an automated tool (weaponizer). Increasingly, client application data files such as Adobe Portable Document Format (PDF) or Microsoft Office documents serve as the weaponized deliverable.
- Delivery - Transmission of the weapon to the targeted environment. The three most prevalent delivery vectors for weaponized payloads by APT actors, as observed by the Lockheed Martin Computer Incident Response Team (LM-CIRT) for the years 2004-2010, are email attachments, websites, and USB removable media.
- Exploitation - After the weapon is delivered to victim host, exploitation triggers intruders’ code. Most often, exploitation targets an application or operating system vulnerability, but it could also more simply exploit the users themselves or leverage an operating system feature that auto-executes code.
- Installation - Installation of a remote access trojan or backdoor on the victim system allows the adversary to maintain persistence inside the environment.
- Command and Control (C2) - Typically, compromised hosts must beacon outbound to an Internet controller server to establish a C2 channel. APT malware especially requires manual interaction rather than conduct activity automatically. Once the C2 channel establishes, intruders have “hands on the keyboard” access inside the target environment.
- Actions on Objectives - Only now, after progressing through the first six phases, can intruders take actions to achieve their original objectives. Typically, this objective is data exfiltration which involves collecting, encrypting and extracting information from the victim environment; violations of data integrity or availability are potential objectives as well. Alternatively, the intruders may only desire access to the initial victim box for use as a hop point to compromise additional systems and move laterally inside the network.
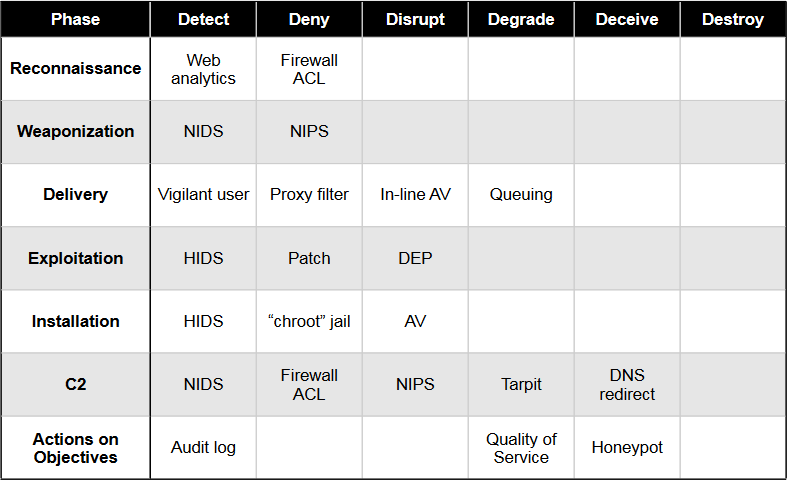
The intrusion kill chain becomes a model for actionable intelligence when defenders align enterprise defensive capabilities to the specific processes an adversary undertakes to target that enterprise. Defenders can measure the performance as well as the effectiveness of these actions, and plan investment roadmaps to rectify any capability gaps. Fundamentally, this approach is the essence of intelligence-driven CND: basing security decisions and measurements on a keen understanding of the adversary.
The courses of action can be split into:
- detect
- deny
- disrupt
- degrade
- deceive
- destroy
And mapped to the Intrusion Kill Chain like this:
Relevant Note(s): Unified Kill Chain Threat Modeling