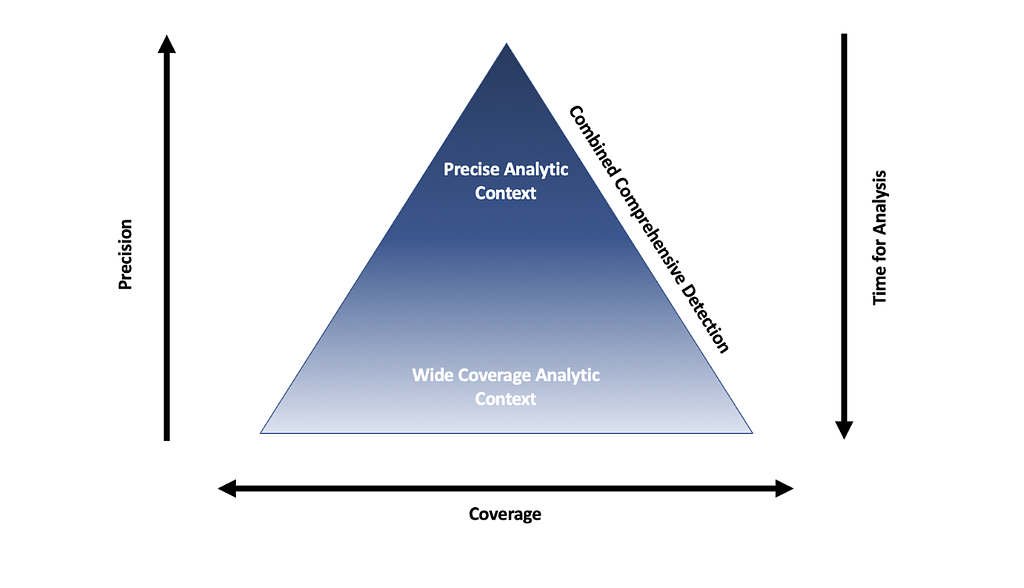
Comprehensive Detection
Currently, organizations are writing single precise detections for the techniques along the different tactics of the kill-chain in the hopes that if an adversary attacks, one of the detections along the chain will trigger.
These detections must be precise, as the false positive rate would cause Alert Fatigue, but this choice poses an inherent risk: blind spots
To address this risk, security organizations want to compliment precise detections with layered broad detections to provide a comprehensive approach to detecting an attack technique.
Precise Detections
Precise detections are often brittle and easy to evade, through for example command line obfuscation, but they still shouldn't be neglected. They provide "quick-wins" as the time to triage is significantly lower than with broad detections and the false positive rate is also very low.
We write a detection focusing on the characteristics of a specific tool commonly used for the technique, like:
- File Hashes
- Command Line Arguments
- Folder Paths used to dump the output
It's desirable to have multiple of these detections, as the likelihood will increase that at least one of them will trigger.
Layered Broad Detections
In contrast to precise detections, broad detections try to detect the moments of the "life cycle" of a technique. This is done by defining choke points an attack has to pass through and then detecting on those.
We want to detect Kerberoasting, then this attack will have to pass these choke points:
- Low Prevalence File Creation (e.g.: Rubeus)
- Process Connecting to KDC over Port 88
- Logon Events (Service Accounts)
To speed up the time to triage, these stages can also be mentioned in the alert, but be sure to make it clear that these are soft links and do not have to trigger to indicate an attack! The detections for the individual choke points can still be bypassed, or alternative paths can be used to complete the technique.
These detections aid the analyst by provide additional with context to determine if the collected events are malicious or benign. Many times the triage decision is based on organic experience biased towards the history of the analysts themselves. However, defenders stand to make a better choice when they have programmatically gathered as much context related to the events as they can.
Relevant Note(s): Defense in Depth Detection Spectrum